Cyber Security for Industrial Automation and Control Systems (IACS)
The cyber security study will be carried out as per guidelines given in IEC 62443 international standard.
IEC 62443-3-2 sets the requirements for risk assessment leading to the identification of zones and conduits for the Industrial automation and control systems (IACS). Based on the detailed risk assessment for each zone and conduit, the sufficient security level target for each could be determined.
FEED Phase Cyber Security Study
The recommended steps for the FEED Phase cyber security study are given below:
- Identification of the system under consideration
- High-level cyber security risk assessment
- Partition the system under consideration into zones and conduits
- Detailed cyber security risk assessment of zones and conduits
The brief description of the each step is given below:
Identification of the system under consideration
Input Required
- Initial system architecture diagrams and inventory.
- Initial network topology diagrams for all packages that will be included in the IACS.
What should input look like:
- High-level network topology diagrams.
- Example diagram.
- Systems communication within and external to the system under consideration.
High-level cyber security risk assessment
The high-level risk assessment is used to determine the business and HSE impact in the event of system compromise or failure. The purpose of the high-level risk assessment is to identify the worst-case unmitigated risk to the system under consideration. The output of a high-level risk assessment will be input to the grouping of assets into zones and conduits and the detailed risk assessments.
The target group for the high-level risk assessment includes stakeholders who may have limited in-depth knowledge of cyber security risks. The high-level risk assessment is documented in a manner that allows all stakeholders to get a clear overview of the high-level cyber risk picture.
The high-level risk assessment is usually based on a review workshop. The output should be presented to appropriate local/regional asset owners and stakeholders.
Input required
- Corporate risk matrix, business impact assessments, disaster recovery plans, incident response plan, functional specifications, etc.
- Relevant safety assessments (such as a safety requirements specification).
- Description of asset owner performance standards for safety systems and barriers.
Output
A description of IACS systems in the system under consideration and possible consequences if the systems’ vulnerabilities are exploited, causing the systems to be unavailable or a loss of integrity or confidentiality. Evaluation of what represents the worst-case unmitigated risk.
Partition the system under consideration into zones and conduits
Input Required
- Outputs of the high-level cyber security risk assessment.
- Reference model defined in this document.
What should input look like:
- High-level cyber security risk assessments. Consider the reuse of risk assessments for similar IACS solutions.
- Reuse of zone and conduit drawings for similar projects.
- Reuse of package vendor best practice.
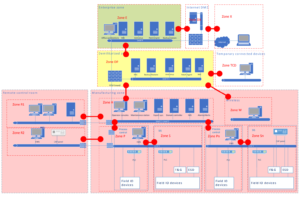
Figure – Example zone and conduit drawing
The following characteristics should be documented for zones and conduits:
- name and/or unique identifier
- physical and/or logical boundary
- entry points (integrations, wireless, remote access …)
- list of external data flows (and internal data flows within a zone)
- assets (equipment and software)
- connected zones
- security requirements
- SL-T
- security policies
- assumptions and dependencies.
Detailed cyber security risk assessment of zones and conduits
The detailed risk assessment is initially conducted in the FEED phase, but is continuously updated, according to similar principles, in the project and operations phase.
The output from the high-level risk assessment and the separation into zones and conduits gives a good overview of the software-based systems that are critical for the operation of the given installation. A detailed risk assessment should be carried out for each zone and conduit. However, it is important to prioritize systems with high consequences where threats are relevant.
The detailed risk assessment is usually based on workshops covering all zones and conduits.
Output: Cyber Security Risk Assessment Report
Cyber Security for Industrial Automation and Control Systems (IACS)
The cyber security study will be carried out as per guidelines given in IEC 62443 international standard.
IEC 62443-3-2 sets the requirements for risk assessment leading to the identification of zones and conduits for the Industrial automation and control systems (IACS). Based on the detailed risk assessment for each zone and conduit, the sufficient security level target for each could be determined.
FEED Phase Cyber Security Study
The recommended steps for the FEED Phase cyber security study are given below:
- Identification of the system under consideration
- High-level cyber security risk assessment
- Partition the system under consideration into zones and conduits
- Detailed cyber security risk assessment of zones and conduits
The brief description of the each step is given below:
Identification of the system under consideration
Input Required
- Initial system architecture diagrams and inventory.
- Initial network topology diagrams for all packages that will be included in the IACS.
What should input look like:
- High-level network topology diagrams.
- Example diagram.
- Systems communication within and external to the system under consideration.
High-level cyber security risk assessment
The high-level risk assessment is used to determine the business and HSE impact in the event of system compromise or failure. The purpose of the high-level risk assessment is to identify the worst-case unmitigated risk to the system under consideration. The output of a high-level risk assessment will be input to the grouping of assets into zones and conduits and the detailed risk assessments.
The target group for the high-level risk assessment includes stakeholders who may have limited in-depth knowledge of cyber security risks. The high-level risk assessment is documented in a manner that allows all stakeholders to get a clear overview of the high-level cyber risk picture.
The high-level risk assessment is usually based on a review workshop. The output should be presented to appropriate local/regional asset owners and stakeholders.
Input required
- Corporate risk matrix, business impact assessments, disaster recovery plans, incident response plan, functional specifications, etc.
- Relevant safety assessments (such as a safety requirements specification).
- Description of asset owner performance standards for safety systems and barriers.
Output
A description of IACS systems in the system under consideration and possible consequences if the systems’ vulnerabilities are exploited, causing the systems to be unavailable or a loss of integrity or confidentiality. Evaluation of what represents the worst-case unmitigated risk.
Partition the system under consideration into zones and conduits
Input Required
- Outputs of the high-level cyber security risk assessment.
- Reference model defined in this document.
What should input look like:
- High-level cyber security risk assessments. Consider the reuse of risk assessments for similar IACS solutions.
- Reuse of zone and conduit drawings for similar projects.
- Reuse of package vendor best practice.
Figure – Example zone and conduit drawing
The following characteristics should be documented for zones and conduits:
- name and/or unique identifier
- physical and/or logical boundary
- entry points (integrations, wireless, remote access …)
- list of external data flows (and internal data flows within a zone)
- assets (equipment and software)
- connected zones
- security requirements
- SL-T
- security policies
- assumptions and dependencies.
Detailed cyber security risk assessment of zones and conduits
The detailed risk assessment is initially conducted in the FEED phase, but is continuously updated, according to similar principles, in the project and operations phase.
The output from the high-level risk assessment and the separation into zones and conduits gives a good overview of the software-based systems that are critical for the operation of the given installation. A detailed risk assessment should be carried out for each zone and conduit. However, it is important to prioritize systems with high consequences where threats are relevant.
The detailed risk assessment is usually based on workshops covering all zones and conduits.
Output: Cyber Security Risk Assessment Report